Hacking Tools: C99 Shell
What is a web shell?: C99 Shell #
shell ( C99 Shell ) A web-based script is a script that is often uploaded to a hosting server with the aim of giving hackers the ability to remotely control your hosting site.
Web servers that become infected can either be internal to the network or sites hosted on the Internet, where the shell is used to gain control over the internal hosts of the Internet server (alert (TA15-314a)).
Hackers can use any language to write a web shell as long as it is supported by the web server.
Some of the most common web shells are in languages that are widely supported, for example, PHP.
Hackers can identify vulnerabilities that can be exploited and some kind of web shell is installed using network scanning tools. For example, these vulnerabilities occur in web server software, content management systems, or CMSs.
Once they are successfully loaded, hackers can use the missiles to take advantage of other exploitation techniques to issue commands and escalate intrusions remotely.
TA15-314a #
Controls are directly related to the functionality or opportunity of the server and may include the ability to delete, add, and execute files, as well as the ability to run additional executables, commands, or scripts (alert (TA15-314a)).
Web shells can also be used intentionally and legitimately by a server administrator at LifeHost to perform actions on the server, for example, reading system logs, creating a user and restarting a service.
Unlike some other types of shells such as reverse shells that need a secondary program to operate on the victim’s machine, a web shell does not need a socket to connect and often runs over HTTP (Paganini, 2016).
They are backdoors that operate from the browser. As such, these tools are tools of exploitation.
Before it can be used to harm the user, a vulnerability must be found in the target application.
There is a way that hackers use through a page to download the file through the site’s programming, for example, the submission form on the Internet site and then
Use of lfi or local file embed vulnerability in the application to include a shell in its pages (paganini, 2016).
What did Hyyat Host protect? #
We guarantee it ( C99 Shell )
The commands in it are not executed outside the user’s powers, meaning that it cannot be crossed from one user to another on our hosting servers.
We also offer a free checking system for the customer on our hosting account, for example, the cxs program that inspects the site and sends a report to the customer and also sends any files infected with the site to the customer. The programmer in shortening the time and identifying the weaknesses that occurred in his site
c99 web shell #
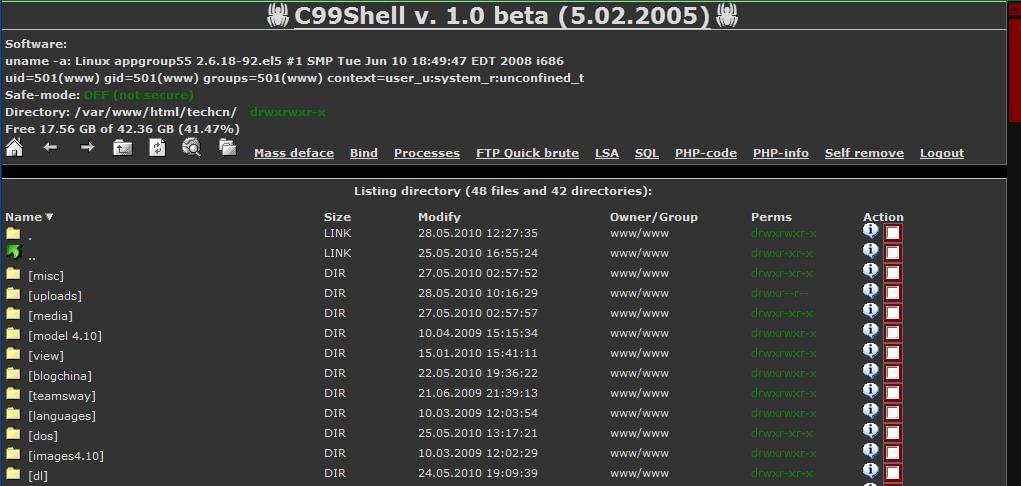
An excellent example of a web shell is the c99 variant, which is a PHP malware often downloaded into a vulnerable web application to give hackers an interface.
The c99 shell allows an attacker to take control of an Internet server’s operations, allowing him or her to give commands on the server as an account under which the threat is running.
It allows the hacker to upload, browse the file system, edit and view files, in addition, to delete, move and change permissions. Finding a c99 shell is an excellent way to identify a compromise on a system.
The c99 shell is about 1500 lines long, and some of its features include showing security measures the web server may use, a file viewer with permissions, and a place where an attacker can operate a custom php code (php malware c99 shell).
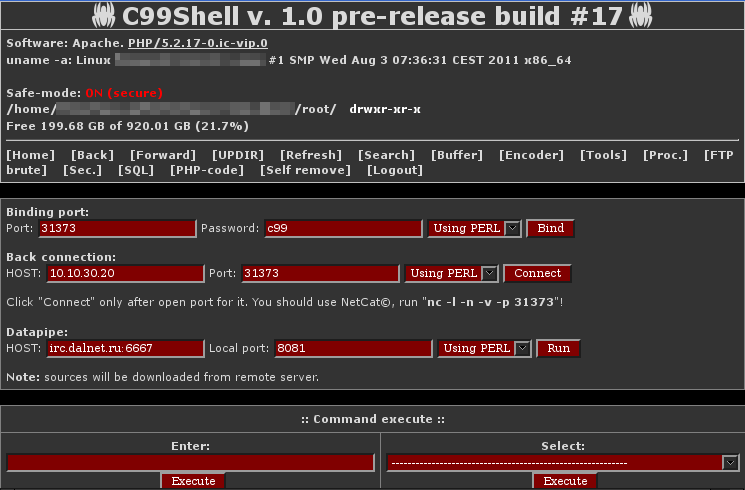
There are different types of C99 shell that are used today. Below is an example of another relatively recent one.
It has several signatures that can be used to write preventive countermeasures.
We put you pictures of some forms of PHP malware c99 shell
Hacking tools explained: C99 Shell
Greetings from the Hyyat Host team