Phishing emails
How does the phishing process take place? #
Phishers send fake e-mails asking the user to update their data as a precautionary measure. These messages often contain links that direct the user to fake websites designed only to steal user information. Some may ask how the hacker or data thief got your mail, and the answer is by the domain name ownership data whois
For example, the user is directed to a fake control panel page, and the user enters the password and password, thinking that it is a reliable page, and when entering it, the person who steals the data will store it, and thus he can enter your site.
Another way is for trolls to unobtrusively download malicious programs onto users’ devices that allow them to access those devices or users’ private information.
The following figure is a simplified illustration of the phishing process
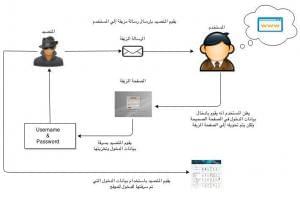
Bogus Invoices: #
It is another type of phishing message, where fake invoices are sent via e-mail or SMS for services or goods requested by the customer.
For example, sending a fake warning message telling the customer that a domain name has expired, and forcing him to pay a fake invoice online using one of the common payment methods.
Common mistakes that enable you to avoid phishing scams: #
- Most phishing emails do not refer to the recipient by name. Instead, it is usually a generic greeting without mentioning the user’s name.
- Phishing messages usually warn the user that his account will be lost if he does not implement the request addressed to him as soon as possible.
- There are obvious spelling and grammatical errors in phishing messages.
- The link that the user is asked to click appears to direct the user to the correct site. But when you move the mouse pointer on the link, a small window appears showing the real link that will direct the user to the fake site.
- Sometimes the message carries the sender’s email and the recipient’s email is the same as your email, which is malicious software that has been used for a long time.
How can protection from phishing operations? #
- Ensure the content of the message and do not click on any link until after verifying it.
- Do not download files attached to messages that are of unknown origin or are not expected to be received.
- Browse websites using the protected https:// protocol.
- Install antivirus and protection software on computers and ensure that the operating system for the hardware and software used is up-to-date with the latest updates.
- Constantly changing the password and not using a single password for several sites or emails.
- Do not update any data until after checking with the company itself.
- Ensure that the software on your site does not have gaps that allow sending emails and that it is updated to the latest version
- Hayat host offers SpamExperts, which is for checking messages and dealing with them. You can follow its explanations via the following link: Press here
If you are exposed to these messages or any suspicious messages, please follow these steps: #
- Do not respond to any phishing messages.
- Do not click on any unknown source link.
- Contact the technical support department Contact us and provide us with a copy of these messages. We will provide you with a comprehensive examination for free of all the site files.
- Your task is to follow the report and implement what is in it. In case you do not have sufficient experience, you can request paid support through tickets via the link click here.
- Delete messages from the mailbox and make sure the trash is emptied.
Been completed
Explanation of phishing emails




