What is a Slowloris DDoS attack?
Slowloris is a denial-of-service attack program that allows an attacker to crush the target server by opening many HTTP synchronized between attacker and target is maintained.
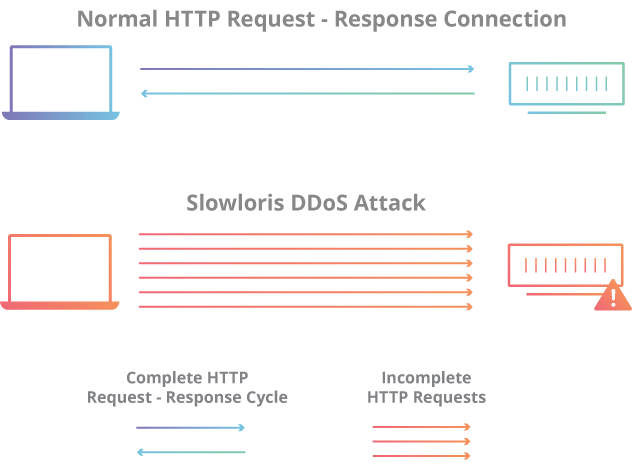
How does the Slowloris DDoS attack work? #
Slowloris is an application layer attack that works through the use of partial HTTP requests. The attack works by opening connections to a targeted web server and then keeping those connections open as much as possible.
Slowloris is not an attack class but instead a specific attack tool designed to allow a single machine to remove the server without using a lot of bandwidth. Unlike DDoS attacks that consume bandwidth such as NTP amplification, this type of attack uses a low amount of bandwidth, and is instead intended to use server resources with requests that appear slower than normal but otherwise mimic normal traffic. They fall into the category of attacks known as “low and slow” attacks. The target server will have too many threads available to handle simultaneous connections. Every thread in the server will try to survive while waiting for the slow request to complete, which never happens. When the maximum number of possible connections to the server is exceeded, every additional connection will not be answered and a denial of service will occur.
Slowloris attack occurs in 4 steps: #
- The attacker first opens multiple connections to the target server by sending multiple partial HTTP request headers.
- The target opens a thread for each incoming request, with the intent of closing the thread once the connection is complete. In order to be efficient, if the connection takes too long, the server will terminate the extremely long connection, freeing the thread for the next request.
- To prevent the target from terminating connections, the attacker periodically sends partial request headers to the target in order to keep the request alive. In essence saying, “I’m still here! I’m just slow, please wait for me.”
- The target server will never be able to release any of the open partial connections while waiting for the request to finish. Once all available threads are used, the server will not be able to respond to additional requests from normal traffic, resulting in a denial of service.
The key behind Slowloris is its ability to cause a lot of trouble while consuming very little bandwidth.
How to mitigate a Slowloris DDoS attack? #
For web servers exposed to Slowloris, there are ways to mitigate some of the impact. Mitigation options for vulnerable servers can be divided into 3 general categories:
- Increased Server Availability – Increasing the maximum number of clients a server can allow at any one time increases the number of connections an attacker must make before they can overload the server. Realistically, an attacker might scale the number of attacks to overcome server capacity regardless of the increments.
- Incoming Requests with Price Limit – Restricting access based on certain usage factors will help mitigate Slowloris’ attack. Techniques such as limiting the maximum number of connections allowed to a single IP address, limiting slow transfer speeds, and the maximum time a client is allowed to stay connected are all ways to limit the effectiveness of low and slow attacks.
- Cloud-Based Protection – Use a service that can act as a reverse proxy, protecting the original server.
Regards Hayat Host< /a> #




